
5 Common VPN Security Risks and How to Overcome Them
We all know how VPNs can improve online privacy. They help you stay anonymous, they keep your data away from snooping eyes, and they’re pretty much standard if you’re working remotely or using public Wi-Fi. But just like with any technology, there are trade-offs. Things can go wrong if you’re not careful. And today, we’re going to talk about the most common VPN security risks and how you can protect yourself without overcomplicating it.
Why VPN Security Measures Matter Now More Than Ever
VPNs aren’t niche tools anymore. They’ve gone mainstream. Millions of people use them daily to log into work, stream from other countries, or just add a layer of privacy to their browsing. And with the growing popularity of remote work, VPN adoption has surged. According to a global survey, seven out of ten respondents mentioned access for remote employees as the main reason for their VPN use.
Attackers have picked up on this shift too. VPN infrastructure is no longer a side target – it’s front and center. Over the past year, we’ve seen many loud cases, from state-sponsored groups to smaller opportunistic attacks. Just one example: Iranian hackers maintained access to critical infrastructure in the Middle East for two years via VPN flaws. And that’s not a one-off.
Misused VPNs have quietly become one of the easier ways into systems that were never meant to be exposed. That’s why VPN security becomes such an important part of the equation.
Top 5 VPN Security Risks You Should Know About
So let’s break it down. What kind of VPN security issues are we actually talking about here? Let’s count them off one by one. We ended up with five.

1. Unpatched VPN Vulnerabilities and Misconfigurations
The first (and maybe the most common) VPN security risk is outdated software. And it’s a real problem.
Here’s how it happens: a company or even a solo user sets up a VPN, it works fine, and then they leave it alone. Meanwhile, attackers are constantly scanning the internet for exposed VPN endpoints. And when they find one running an old version with a known flaw? That’s their entry point.
Take Ivanti Connect Secure in late 2024 / early 2025, for example. A zero‑day VPN vulnerability (CVE‑2025‑0282) allowed unauthenticated remote code execution. Attackers exploited it in the wild, installing web shells and backdooring VPN devices. That gave them access to thousands of networks. It wasn’t even a secret (there were security advisories and patches available). But not everyone applied them in time. These flaws don’t stay quiet for long. Once they’re public, they get picked up fast, by ransomware crews, state-sponsored groups, or whoever’s looking to get in.
So the fix here is obvious, but it takes discipline.
- Keep your VPN software updated, set reminders if you have to.
- Change default passwords immediately, and use long, unique ones.
- Turn off unused services.
- And check your config once in a while, especially after major updates.
- If your VPN supports MFA, turn it on.
These are low-effort steps that stop a huge chunk of real-world attacks.
2. Data Leaks and Connection Drops
This next issue is closely related to the first. A VPN can be running fine on the surface, but still leaking data behind the scenes if it’s not set up correctly.
The most common offenders are: DNS leaks and WebRTC leaks. These happen when your device bypasses the encrypted tunnel and sends certain types of traffic (like DNS requests or browser metadata) over your regular internet connection. That can expose your real IP address, your location, or the sites you’re visiting, even if you think everything’s going through the VPN.
And then there’s dropped connections. If your VPN disconnects, even for a second, and your device automatically falls back to your regular connection, traffic goes out unencrypted. That might be fine if you’re reading the news, but if you’re signing into something sensitive, that brief disconnect could spill more than you’d want. That’s why tools like kill switches exist.
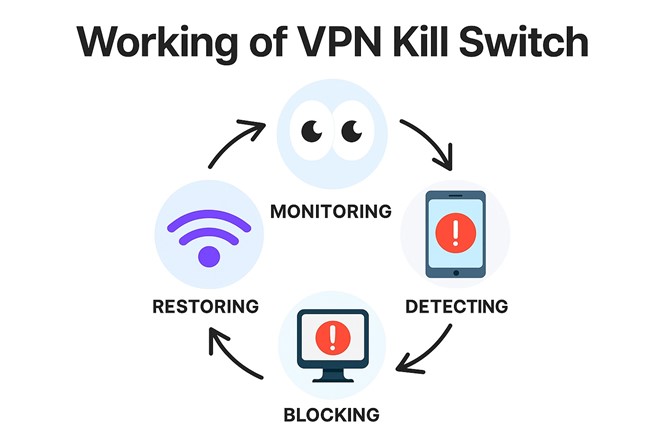
A kill switch isn’t complicated – it’s just a setting that says “if the VPN drops, stop all internet traffic until it’s back up.” Most good VPN apps include this, but not all of them turn it on by default. You have to dig into the settings and flip the switch yourself.
Also, if you were in the middle of uploading something important, you could lose that data in the process. We’ve seen cases where someone thought a file was fully transferred, deleted the original, and later discovered the VPN dropped mid-transfer, leaving them with a corrupted copy. At that point, the only option might be trying to use data recovery software to retrieve the original file. So a stable VPN connection is more important than it might seem.
What can you do:
- First, enable that kill switch.
- Second, use the VPN’s built-in DNS server, not your ISP’s.
- And third, if your VPN drops often, consider switching servers or even providers. Stability matters.
3. Malware and Malicious VPN Apps
Another very common VPN vulnerability, and one that’s gotten worse over time, is malicious VPN apps. These are apps that claim to be VPNs, security tools, or “optimizers,” but in reality they’re doing something else: stealing data, injecting ads, or worse.
You’ve probably heard about the scandal around VexTrio. That’s a perfect example. In 2025, researchers discovered that VexTrio was pushing fake VPNs and spam-blocker apps on Apple’s App Store and Google Play. These apps looked legit, but they harvested personal info and flooded devices with ads. And that sadly wasn’t an isolated case.
It’s often hard to spot a malicious app on your own. They’re designed to blend in – clean UI, familiar names. So it’s worth slowing down. Whether it’s a free or paid VPN, make sure you’re choosing a VPN from a provider with a solid track record. Check real user reviews, not just the star rating.
And don’t rush to install something that was released last week with no history behind it.
4. Weak Encryption and Outdated Protocols
Here’s one that doesn’t get talked about enough: the actual encryption behind your VPN. A lot of users assume that if the VPN is connected, the tunnel must be secure. But that’s not always true, especially if the service is using old protocols or weak ciphers behind the scenes.
Some VPNs still support outdated protocols like PPTP or old versions of L2TP/IPsec, which are no longer considered safe.
- PPTP, for example, can be cracked in hours with widely available tools.
- And with L2TP, if it’s not paired correctly with strong encryption, it’s basically just a wrapper that adds no real protection.
We’ve seen this come up in forums and Reddit threads where users set up their own VPN servers, left default settings on, and unknowingly forced all connections through outdated configurations. People might realize months later that they had been running with 128-bit encryption while thinking they had 256. Nobody warned them; the VPN client didn’t show it clearly.
It’s also a problem with “lite” or free VPN services that don’t disclose what encryption they’re actually using. If you dig into the settings and see options like “Automatic,” or it doesn’t let you choose the protocol at all, there’s a good chance it’s falling back to something less secure.
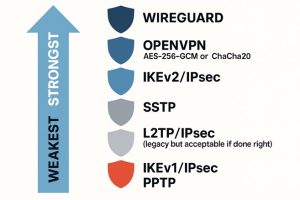
So what should you do? Stick with modern protocols like OpenVPN, IKEv2, or WireGuard. These are widely trusted, well-audited, and use strong encryption (AES‑256 or ChaCha20). And don’t rely on automatic mode – go into the settings and check what protocol is actually being used. If your VPN doesn’t show that info clearly, that’s a sign to switch providers.
Also, if you’re setting up your own VPN server (like with OpenVPN or WireGuard), follow the latest security recommendations. Don’t copy old tutorials. Don’t reuse configuration files from threads written in 2017. Crypto standards move fast. Your VPN should too.
5. Logging and Privacy Risks (Untrusted Providers)
And finally, we have one of the biggest long-term risks: using a VPN you can’t fully trust.
Here’s the thing: when you connect to a VPN, you’re basically handing over all your internet traffic to the VPN provider. Your ISP can’t see what you’re doing anymore, but your VPN can. So if that provider is logging your activity, keeping metadata, or storing connection timestamps, you’re not really private (you’ve shifted trust from one company to another).
Most people don’t think about this. They install a VPN, see “no logs” on the homepage, and move on. But not all no-logs claims are legit. Some services say it as a marketing line, but keep connection records “for diagnostics,” or store data that could still tie activity back to a specific user.
We’ve seen incidents where VPN providers were forced to hand over logs they weren’t supposed to have. And in 2024, over 2 million VPN credentials were leaked through malware campaigns targeting multiple services (ProtonVPN, NordVPN, and Surfshark among them).
While most of these weren’t direct server hacks, the result was still a major VPN data breach that exposed just how much damage can come from a single compromised account.
- So choose a VPN provider you can trust, one that takes security seriously on both the technical and user-facing side. It’s not just about picking a fast server or a slick app. It’s about putting your data in good hands.
- Don’t reuse passwords between services, especially for VPN accounts. If your email and VPN login are the same, and you’re not using two-factor authentication, you’re a soft target for credential stuffing.
- Also, think about how much info you’re handing over during sign-up. Some VPNs let you create an account without email. Some accept cryptocurrency. Others require full billing info and tie your account to your real name. None of that is wrong, but you should be aware of what kind of trace you’re leaving behind.
The VPN provider becomes your new ISP in terms of visibility. If you wouldn’t trust your ISP with your data, don’t blindly trust your VPN either. Do the homework.
Final Thoughts
We didn’t walk through all these VPN risks to scare you or to dissuade you from using a VPN. Honestly, it’s the opposite. A good VPN is still one of the simplest ways to protect your privacy, stay secure on public Wi-Fi, and get access to stuff you normally couldn’t. But you also shouldn’t ignore the dangers of VPN misuse.
If you take a few minutes to check the settings, stay up to date, and follow the VPN security measures we talked about above, you’ll avoid most of the problems people run into. None of this is overly technical. It’s about not leaving the door wide open.
So use a VPN. Use a good one just like iProVPN. And use it smart.





